
Juice jacking: What is it?
We’ve come to rely on our smartphones to help complete daily tasks, and this has resulted in the need to recharge our phones multiple times

We’ve come to rely on our smartphones to help complete daily tasks, and this has resulted in the need to recharge our phones multiple times

Virtualization is the act of moving a physical component or bit of software from a physical environment to a digital one that’s normally delivered over

When transitioning from traditional phone systems to Voice over Internet Protocol (VoIP) solutions, people often overlook the way calls are put on hold. However, doing

Any business owner worth their salt knows the value of data to business. This is why it’s bizarre that many business owners don’t have a
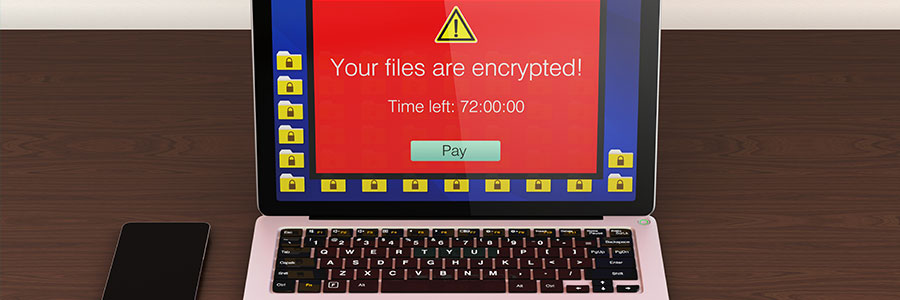
We’ve gotten so caught up discussing ransomware prevention with our clients that we’ve neglected to mention that several strains have already been defeated. In fact,

The intricacies of business technology are not the easiest to understand. Complicated explanations usually lead to misunderstandings, and this is especially true for virtualization. Here

When it comes to business-related searches, Google is second to none. But despite being the industry leader in search engines, this powerhouse is never complacent.
Many businesses still rely heavily on landline telephones, which remain one of the first points of contact businesses have with their customers. With the marriage
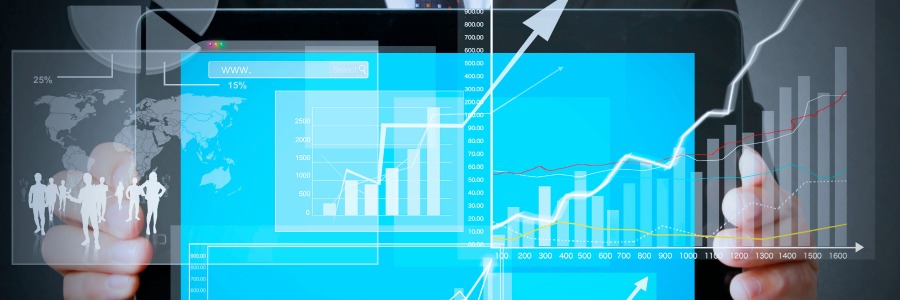
A dashboard is a business intelligence tool that displays metrics and key performance indicators (KPI) for organizations. Dashboards give you an overall view of your

Social media phishing is on the rise. Facebook is one of the most commonly impersonated brands in phishing attacks. Hackers now employ more sophisticated tactics,
Trust Bonded Networks with your IT needs and experience the peace of mind that comes with having a reliable, responsive, and dedicated IT partner by your side. Together, let’s make IT a breeze, not a burden.